A dull attempt to hack into my email from Nigeria.
Published Date: 2022/11/03 by: DaVieS
  |
Seems like this amazing African country has some hacky potential, but so much to learn.
The thing why is this attempt worth a blog entry, because he unable to get any information, but exposed himself and this award-winning dull attempt should be worth to talk.
Well Done!
I got a phising email (Of Corse) from AMAZON-AWS instance that pretending that my system has became self-aware and sending under (my name) an email to change my password immediately.
ASPF-FINGERPRINT: SOA:
ASPF-FINGERPRINT: PTR: ec2-100-26-95-170.compute-1.amazonaws.com
ASPF-FINGERPRINT: IP: 100.26.95.170
ASPF-FINGERPRINT: ELO: ip-172-26-0-145.ec2.internal
ASPF-FINGERPRINT: LOC: North America / United States
ASPF-FINGERPRINT: SRV: 14618 AMAZON-AES
ASPF-DATE: Wed, 02 Nov 2022 14:35:01 GMT
Subject: [SPAM] URGENT ACCOUNT VALIDATION SERVICE!
Dear davies,
This is a second notification message sent from our database that your email account
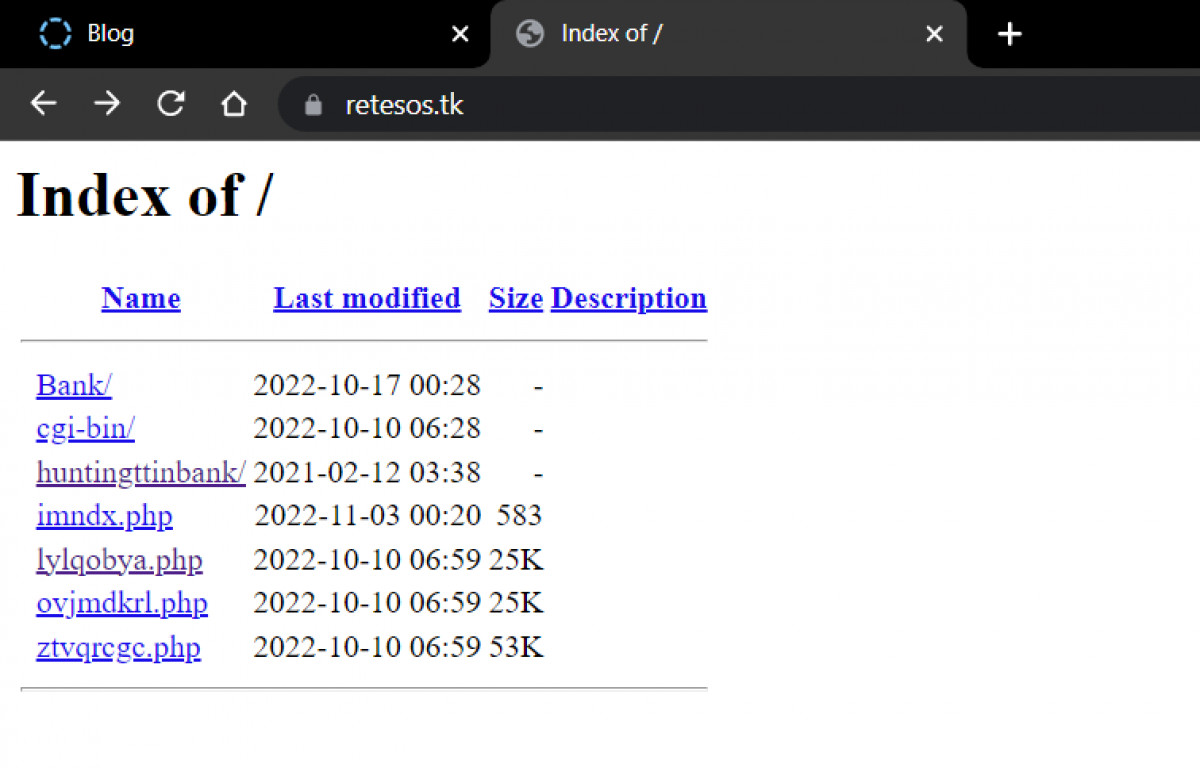
davies@npulse.net will expire within the next 48 hours and access to your account might be terminated.And the only one button goes forward to: https://retesos.tk/imndx.php/?email=davies@npulse.net
retesos.tk
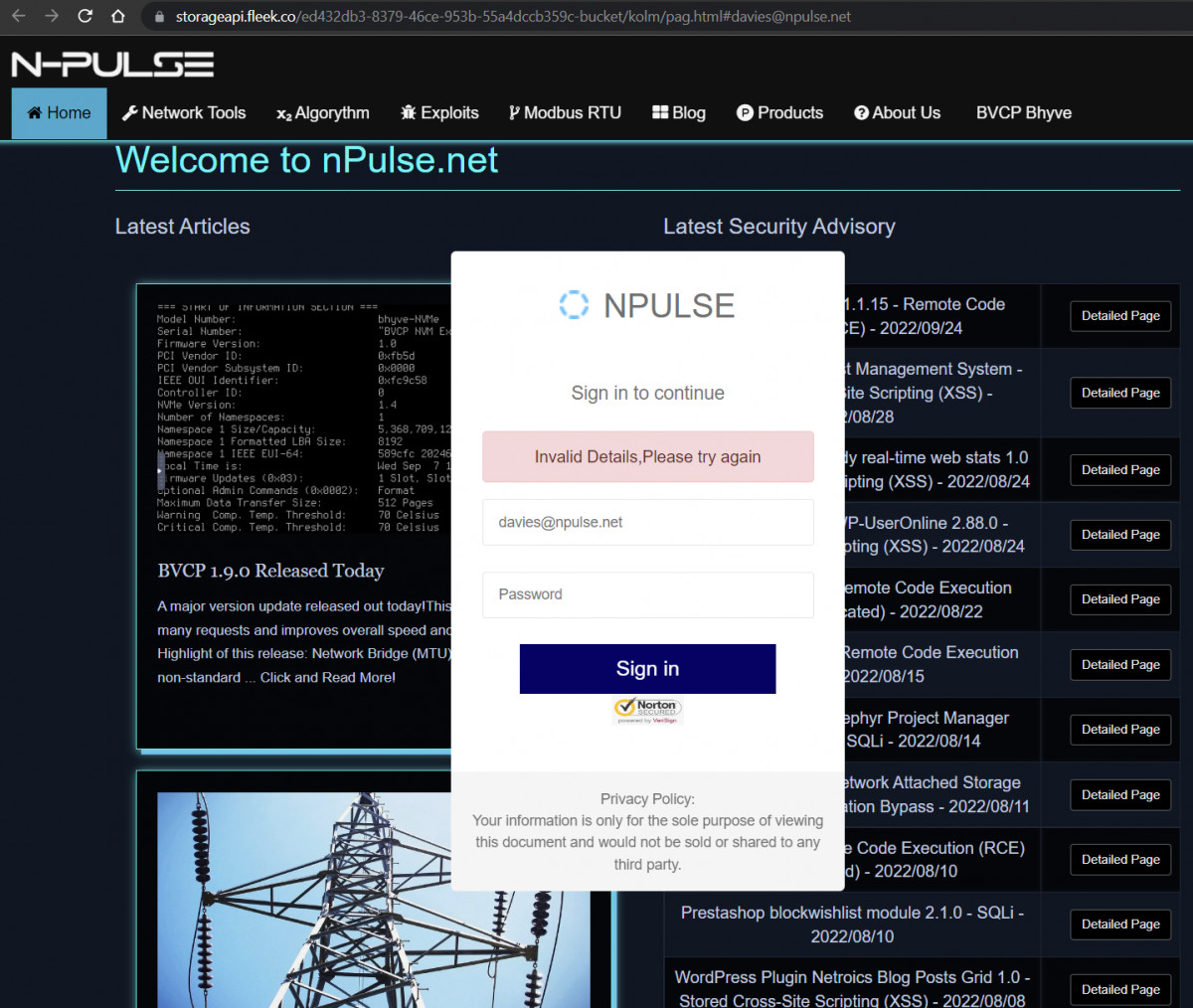
86.48.1.128 vmi1030152.contaboserver.net 254 Europe / Denmark Sentia Denmark A/SThen this site forward to https://storageapi.fleek.co/ed432db3-8379-46ce-953b-55a4dccb359c-bucket/kolm/pag.html#davies@npulse.net
(Just to mention I already submitted reports against fleek.co, coz all the attacking attempts comes from their side so I think this is not coincidence anymore)
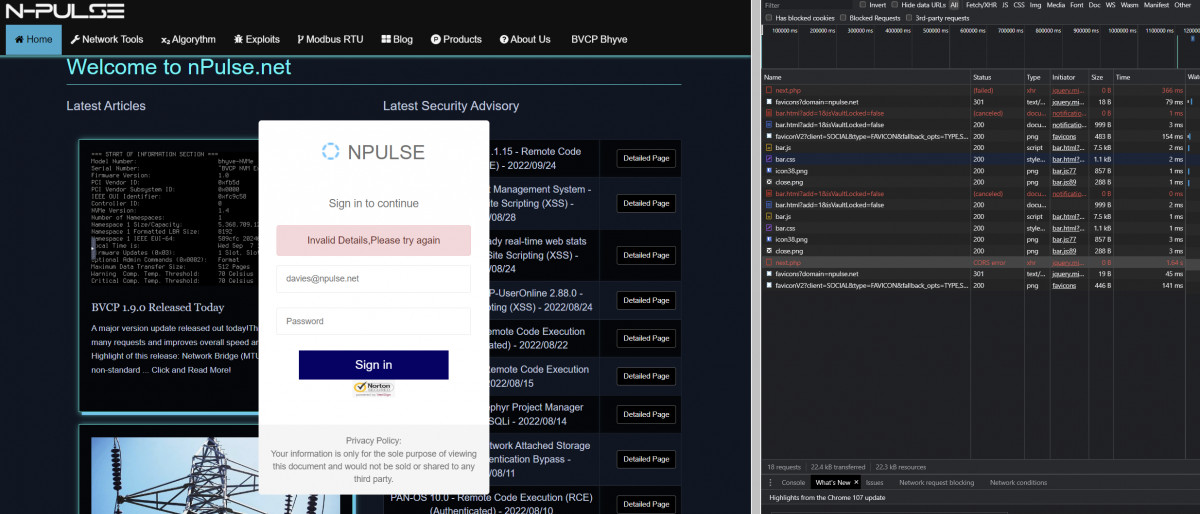
So the fleek.co provides a website to show a HTML form that pretending to be nPulse.net which is infringing and also a felony attempt, and asking for an email and password.
After filling the form with the right details, it is become submitted into https://52.37.77.10/ojo/next.php
52.37.77.10 ec2-52-37-77-10.us-west-2.compute.amazonaws.com 0 North America / United States AMAZON-02
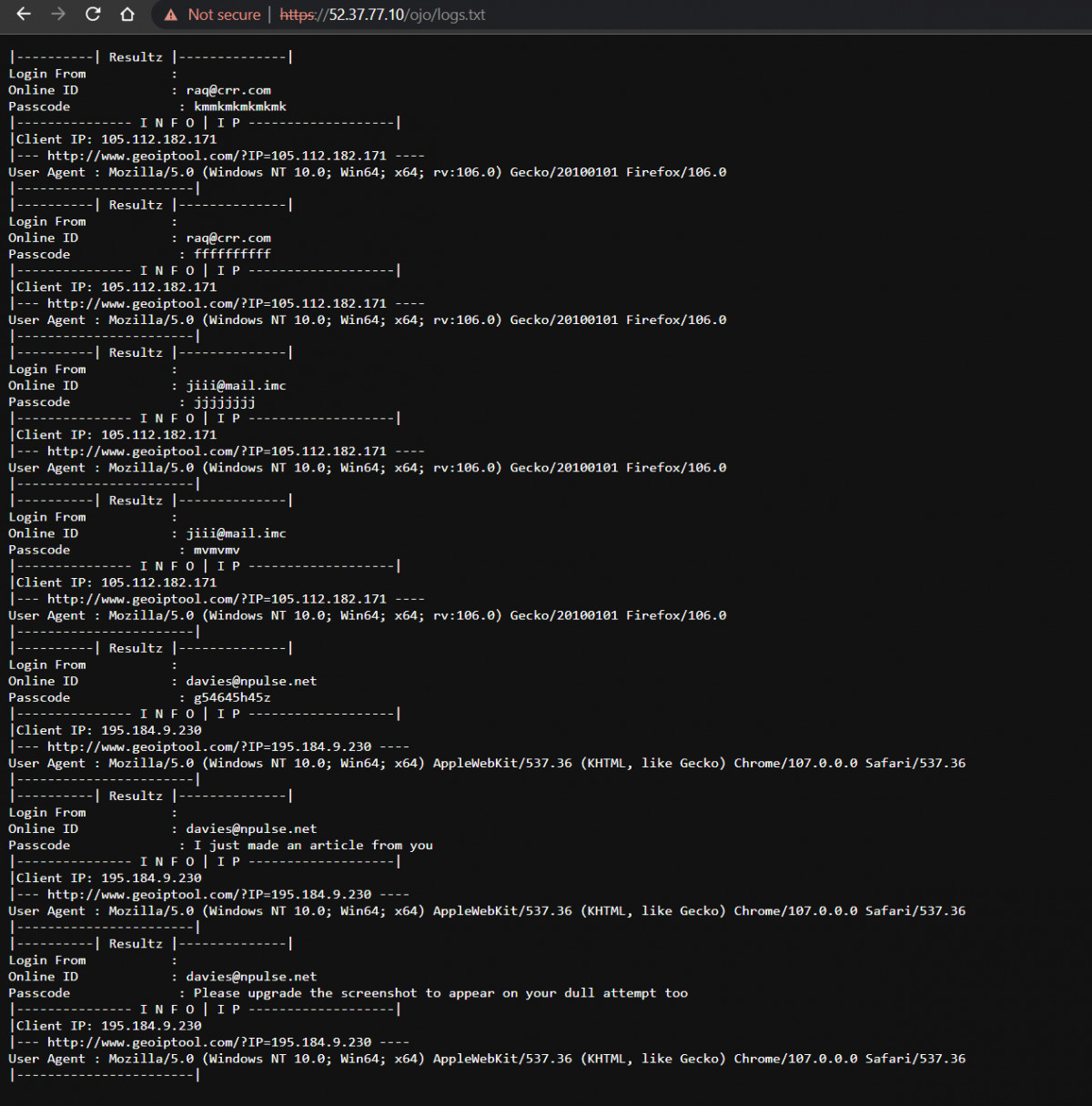
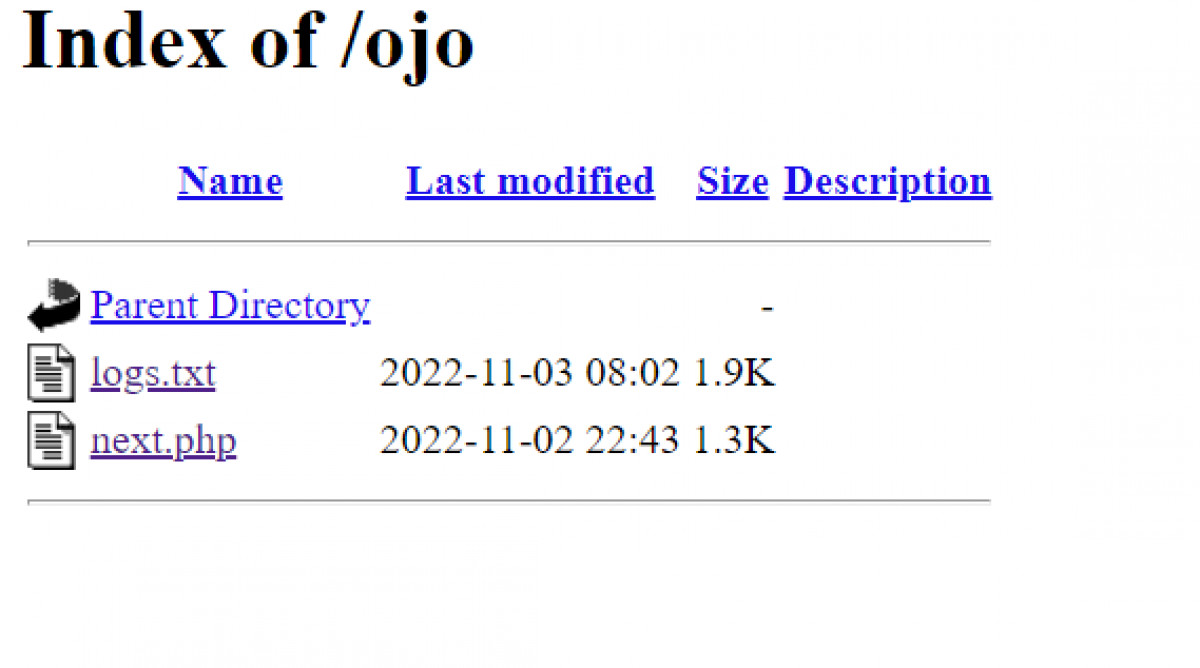
This server has a directory listing enabled and thats why it clearly advertising that it has a logs.txt.
Guess what the logs.txt has? An attacker test attempts from his own IP Addresses and details.
https://52.37.77.10/ojo/logs.txt
|----------| Resultz |--------------|
Login From :
Online ID : raq@crr.com
Passcode : kmmkmkmkmkmk
|--------------- I N F O | I P -------------------|
|Client IP: 105.112.182.171
|--- http://www.geoiptool.com/?IP=105.112.182.171 -
User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
|-----------------------|
|----------| Resultz |--------------|
Login From :
Online ID : raq@crr.com
Passcode : ffffffffff
|--------------- I N F O | I P -------------------|
|Client IP: 105.112.182.171
|--- http://www.geoiptool.com/?IP=105.112.182.171 -
User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
|-----------------------|
|----------| Resultz |--------------|
Login From :
Online ID : jiii@mail.imc
Passcode : jjjjjjjj
|--------------- I N F O | I P -------------------|
|Client IP: 105.112.182.171
|--- http://www.geoiptool.com/?IP=105.112.182.171 -
User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
|-----------------------|
|----------| Resultz |--------------|
Login From :
Online ID : jiii@mail.imc
Passcode : mvmvmv
|--------------- I N F O | I P -------------------|
|Client IP: 105.112.182.171
|--- http://www.geoiptool.com/?IP=105.112.182.171 -
User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:106.0) Gecko/20100101 Firefox/106.0
|-----------------------|
|----------| Resultz |--------------|
Login From :
Online ID : davies@npulse.net
Passcode : g54645h45z
|--------------- I N F O | I P -------------------|
|Client IP: 195.184.9.230
|--- http://www.geoiptool.com/?IP=195.184.9.230 -
User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
|-----------------------|
|----------| Resultz |--------------|
Login From :
Online ID : davies@npulse.net
Passcode : I just made an article from you
|--------------- I N F O | I P -------------------|
|Client IP: 195.184.9.230
|--- http://www.geoiptool.com/?IP=195.184.9.230 -
User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
|-----------------------|
|----------| Resultz |--------------|
Login From :
Online ID : davies@npulse.net
Passcode : Please upgrade the screenshot to appear on your dull attempt too
|--------------- I N F O | I P -------------------|
|Client IP: 195.184.9.230
|--- http://www.geoiptool.com/?IP=195.184.9.230 -
User Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
|-----------------------|
105.112.182.171 105.112.182.171 0 Africa / Nigeria Celtel Nigeria Limited t.a ZAIN
Due it is clearly a targeted attempt to gain access to my email address I reported this incident to every provider, and I will keep you posted what these provider did and how much time they required for an appropriate action on their side.
I have to mention that the this LAME method wont work until you manually enable to bypass SSL warning.
To question is why an attacker try his luck on a site which is about network security? - no clue.
 |
 |
 |
 |
|
If you like the article then don't forget to share!
|
||
Is Rust better than C/C++ ?
Rust is relatively new programming language which offers full memory management and garbage collection, while C/C++ already has a decent history..
Network Update
Proudly announcing that in the past days we expanded our infrastructure and our services will become more stable and quickier at us west, us..
Windows 10/11 Disable Search and annoyings on start menu
The one of the most irritative feature on windows is a "new" start menu which sends every input into Microsoft related services. Also if you have..
BVCP 2.0.x Released
Our one of the most popular FREE-TO-USE Software BVCP reached the next milestone.Big thanks to the active community, a ton of feedbacks received..
Welcome 2024
We have been busy at 2023. Im personally very happy to see a lot of new technologies especially EV related researches.We continued to support our..
FreeBSD 14 fresh install breaks mc (Midnight Commander) subshell support
We are very happy to announce that - if you did not know already - one of the best Operating System released a new version. FreeBSD 14. This..
ZFS Replication Software
While we are working on BVCP 2.0 just another software made to handle ZFS Replications over multiple nodes. The software yet not released..
Bhyve UEFI drops into EFI shell, Linux wont boot Easy Workaround
EFI works that way that the installer places a file into a FAT32 partition in a regular directory as called "BOOT". The usual full path of..
Nexus Datalogger 2023
We're proudly present that we released out our next version of datalogger software as commerical product. Our first version of Datalogger..













